Linux Full Disk
Encryption On Ubuntu 14.04 LTS
The full disk
encryption typically used in Linux is DM-Crypt with LUKS. DM-Crypt is
essentially cryptographic system for block devices that uses device
mapper. More information on DM-Crypt can be found here.
LUKS is the Linux Unified Key Setup and is a specification for key
management. More can be found here.
The setup that will
be described in this post will use DM-Crypt and LUKS via the
cryptsetup utility. Also Ecryptfs and LVM will be used.
First the disk
layout should be defined. For this setup there will be a single
removable disk and a standard hard drive. The removable disk can be a
USB drive or some other writable storage device that can be used to
boot from.
The following
represents the encryption layout that will be used.
Boot Ubuntu live
disc in Try Mode.
Start two terminals.
In one terminal
identify the disk for encryption and the disk for /boot
Prepare the
encrypted disk by filling it with pseudo-random data.
sudo dd if=/dev/urandom of=/dev/sda bs=512;
Once complete,
create the encrypted disk.
sudo cryptsetup -c aes-xts-plain64 --hash sha512 --key-size 512 luksFormat /dev/sda;
Open the encrypted
disk.
sudo cryptsetup open –type luks /dev/sda lvm;
Create the LVM
volumes.
sudo pvcreate
/dev/mapper/lvm;
sudo vgcreate system
/dev/mapper/lvm;
sudo lvcreate -L 10G
-n rootvol system;
sudo lvcreate -L
2048M -n swapvol system;
sudo lvcreate -l
100%FREE -n homevol system;
Create partition
table for boot disk.
sudo fdisk /dev/sdb;
n, p, 1, <enter>,
<enter>, w
Make the file
systems.
sudo mkfs.ext4
/dev/mapper/system-rootvol;
sudo mkfs.ext4
/dev/mapper/system-homevol;
sudo mkfs.ext2
/dev/sdb1;
sudo mkswap
/dev/mapper/system-swapvol;
Run the installer
and use the “something else” disk option.
Set the boot disk as
“/dev/sdb” and assign the mountpoints to the corresponding
partitions and volumes.
At the user creation
section. Do not select encrypt home directory.
Once the install is
finished; Continue “testing”.
At this point we
will configure the new OS to use the encrypted disk and encrypt the
user's home directory.
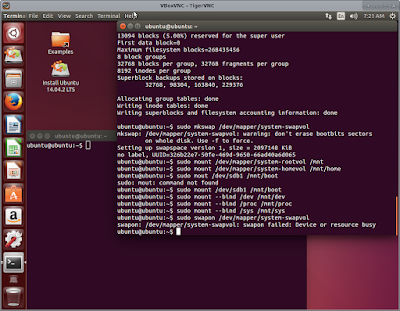
Mount volumes,
partitions, and other FS for chroot.
sudo mount
/dev/mapper/system-rootvol /mnt;
sudo mount
/dev/mapper/system-homevol /mnt/home;
sudo mount /dev/sdb1
/mnt/boot;
sudo mount –bind
/dev /mnt/dev;
sudo mount –bind
/proc /mnt/proc;
sudo mount –bind
/sys /mnt/sys;
sudo swapon
/dev/mapper/system-swapvol;
blkid;
In the second
terminal we will chroot into the newly installed OS and configure it
to boot using the encrypted disk.
sudo chroot /mnt;
ecryptfs-migrate-home
-u user;
vi /etc/crypttab;
“lvm UUID=<ID
from blkid of the encrypted disk, crypto_LUKS> none luks,discard”
save and exit
vi
/etc/initiramfs-tools/conf.d/resume;
“RESUME=/dev/mapper/system-swapvol”
save and exit
update-initramfs -u
-k all -c -v;
exit;
Unmount the /mnt
mount points from terminal one and remove swap.
sudo umount
/mnt/home /mnt/boot /mnt/dev /mnt/proc /mnt/sys /mnt;
sudo swapoff
/dev/mapper/system-swapvol;
Reboot into the
newly installed Ubuntu OS.

















No comments:
Post a Comment